Q1) Which of the following java technologies exists on the web server on the web server machine interactions with the client?
A) Java Servlet
Q2) Which of the following constraints can be directly expressed in the schemas of the data model?
Q4) Which of the following associations is represented as a line connecting the participating classes, and may optionally have a name?
A) Binary
Q5) Which of the following comparison operators does SQL use to compare an attribute value to NULL?
A) 1.IS NOT
2. IS
Q6) Which of the following updates recomputes a view only upon demand?
Q7) Due to which of the following action does a checkpoint record in log also include additional information, and this can facilitate undoing transaction operations in the event that a transaction must be rolled back?
A) Force-write all main memory buffers that have been modified to disk
Q8) Consider the following statement;
"if the validation phase is successful, the transaction updates are applied to the database; otherwise the update are discard and transaction is restarted."
In which of the following phases of concurrence control protocol does this happen?
A) Write
Q9) Which of the following interpretations are true of NULLs?
Each correct answers represent a complete solutions. Choose all that apply.
A)
1. The attribute value for the tuple is unknow.
2. The attribute does not apply to the tuple.
3. The value is know but absent; that is, it has not been recorded yet.
Q10) Which of the following entries is the web site name (URL) of the client user computer?
A) $_SERVER['REMOTE_HOST']
Q11) What challenges are faced by big data technologies when they are used for analytics applications?
Q12) Which of the following steps of ER-to-relational mapping algorithm?
A)
1. Mapping of N-ary relationship types.
2. Mapping of binary 1:1 relationship types.
3. Mapping of week entity types.
4. Mapping of regular entity types.
Q13) Which operation is used for inserting new data or new versions of existing data items?
A) Put
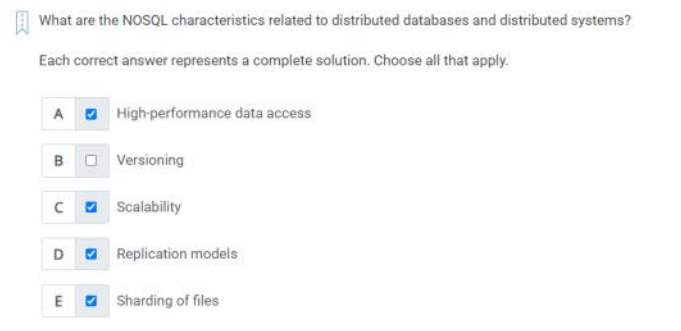
Q14) What are the NOSQL Characteristics related to distributed database and distributed systems?
A)
1. High-performance data access
2. Scalability.
3. Replication models.
4. Sharding of files
Q15) Consider the following statement:
"If the validation phase is successful, the transaction updates are applied to the database; otherwise, the updates are discarded and the transaction is restarted,"
A) Write
Q16) Which of following java technologies exists on the web serve machine and manager interactions with the client?
A) Java Servlet
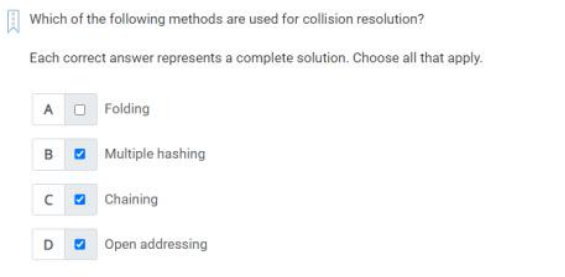
Q17) Which of the following methods are used for collision resolution?
A)
1. Multiple hashing
2. Chaining
3. Open addressing
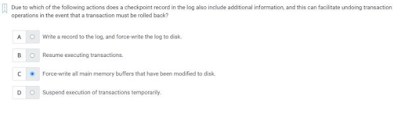
Q18) Due to which of the following actions does a checkpoint record in the log also include additional information, and this can facilitate undoing transaction operations in the event that a transaction must be rolled back?
A) Force-write all main memory buffers that have been modified to dosk.
Q19) Which statistical model provides a framework in which term weighting, ranking of retrieved document, and determining the relevance of feedback are possible?
A) Vector space
Q20) Which of the following types of the commands does the NameNode send to the DataNode?
A)
1.Reregister the node or Shut down the node
2. Remove a block replica
3. Replication a block to another node.
Q21) Which of the following algorithms was the first alogrithm to use the download closure and antimontonicity propertes?
A) Apriori
Q23) During which step of the ARIES recovery procedure is the log scanned backward and the operation of transactions that the operations of transaction that were active at the time of the crash are undone in reverse order?
A) UNDO
Q24) Which spatial operator provides a more specific description of the object's geometry and measure some global properties of single objects?
A) Metric
Q25) Which of the following is described in the given statement?
"Take immediate action to eliminate the attacker's the access to the system and to isolate or contain the problem to prevent further spread."
A) Confinement
Q26) What are the characteristics of a dynamic programming alogrithm?
A)
1. Recursively defines the value of optimal solution.
2. Computers optimal solutions and develops its value in a bottom-up fashion.
3. Develop the structure of an optimal solution.
Q27) Which of the following clauses assigns a variable to range over each of the individual elements in a sequence?
A) FOR
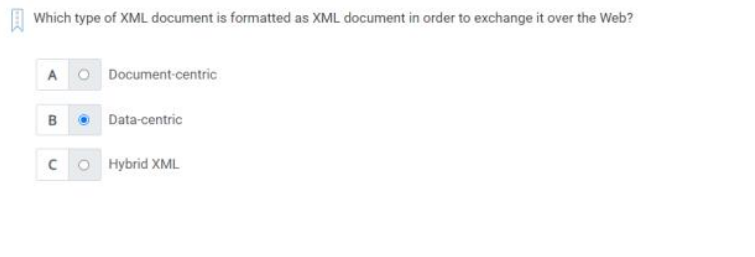
Q28) Which type of XML document is formatted as XML document in order to exchange it over the web?
A) Data-centric
Q29) Consider the following functions:
Allocates resources to applications.
Provides some degree of management of application masters.
manager cluster, doling out resources based on a pluggable scheduling policy.
A) ResourceManager
Q30) Which type of the XML document is formatted as XML document in order to exchange it over the web?
A) Data-centric
Q31) Which of the following interruptions are true of NULLs?
A)
1. The value is know but absent; that is, it has not been recorded yet.
2. The attribute does not apply to the tuple.
3. The attribute value for the tuple is unknow.
Q32) Who is responsible for security breaches and poor system response time problems?
A) Database administrator.
Q33) Which of following entries in the web site name (URL) of the client user computer?
A) $_SERVER['REMOTE_HOST']
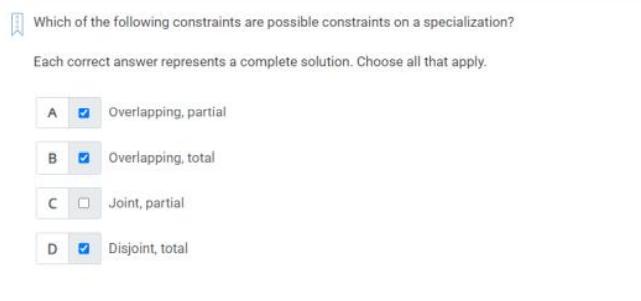
Q34) Which of the following constraints are possible constraints on a specialization?
A)
1. Overlapping, partial
2. Overlapping, total
3. Disjoint, total
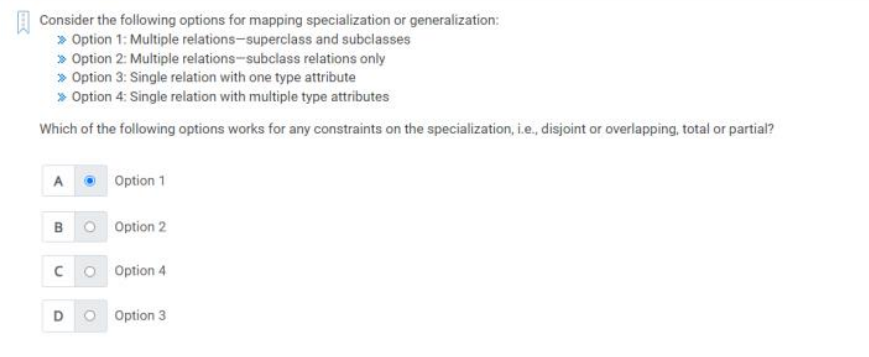
Q35) Consider the following options for mapping specializing or generalization;
Option 1: Multiple relations-superclass and subclasses .
Option 2: Multiple relations-subclass relations only.
Option 3: Single relation with one type attribute.
Option 4: Single relation with multiple type attributes
Which of the following options works for any constraints on the specialization, i.e, disjoint or overlapping, total or partial?
A) Option 1
Q36) Consider the following skills of a surgical technical:
Ability to work in groups
Possesses a calm nature
Excellent communication skills
Willingness to learn
The skills of a surgical technical are an example of which type of attribute?
A) Multivalued attribute.
Q37) During which of the following steps do the database designers interview prospective database used to understand and document their data necessities?
Q39) Consider the following statement:
"Web analysis is used to find interesting usage patters of web sites. If any flew in a web site has been exploited, it can be inferred using web analysis, there by allowing the design of more robust web sites,"
Which application of web analysis does the give statement refer to?
A) Web security
Q40) Who design and implement software packages that facilitate database modeling and design, and improved performance?
A) Tool developers
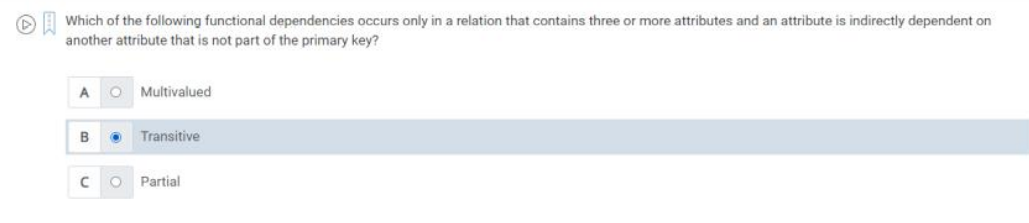
Q41) Which of the following functional dependencies occurs only in a relation that contains three or more attributes is indirectly dependent on another attribute that is not part of the primary key?
A) Transitive
Q42) What will be the next step after importing the JDBC class library when writing a java application program with database access through JDBC function calls?
Q43) Which abstaraction Concept is needed to distinguish among database objects and classes, and to identify database objects?
A) Identification
Q44) Consider the following example:
Q45) Which of the following strategies updates a views as the base tables are changes?
A) Immediate update
Q46) Which of the following indexes requires that the ordering field of the file has a distinct value for each records are of fixed length with two fields ?
A) Primary
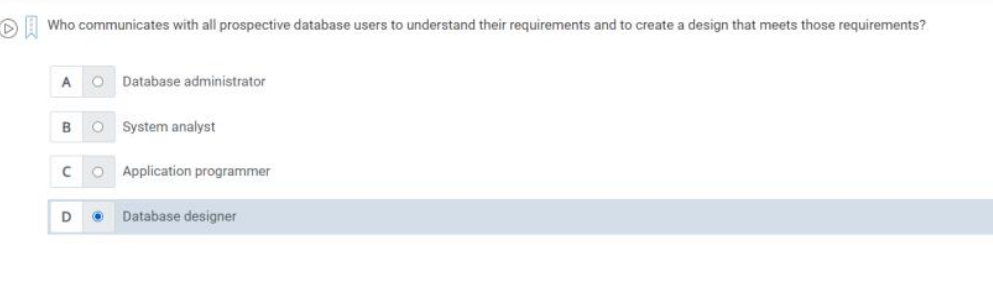
Q47) Who communicates with all prospective database users to understand their requirement and to create a design that meets those requirements ?
Q48) Which stage of a distributed database query is performed locally?
A) Local query optimization
Q52) Which of the following violations will occur when a transaction may read a set of rows from a table, based on some condition specified in the SQL WHERE-clause?
Q53) Which type of end user tries to learn most of the DBMS facilities to achieve their complex requirement ?
A) Sophisticated
Q54) Which of the following properties is enforced by the concurrency control subsystem of the DBMS?
A) Isolation
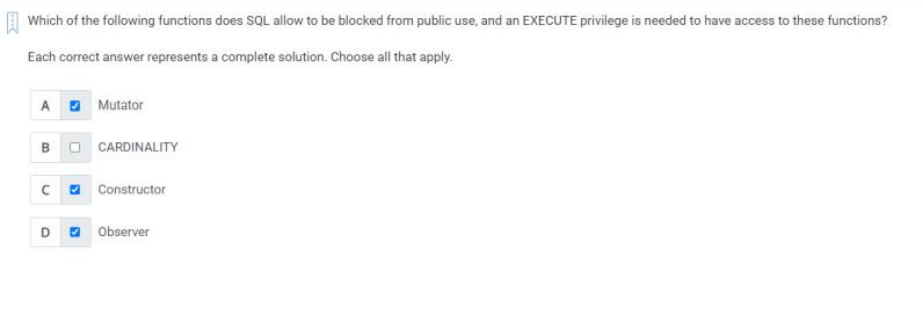
Q55) Which of the following functions does SQL allow to be blocked from public use, and an EXECUTE privilege is needed to have access to these function?
A)
1. Mutator
2. Constructor
3. Observer
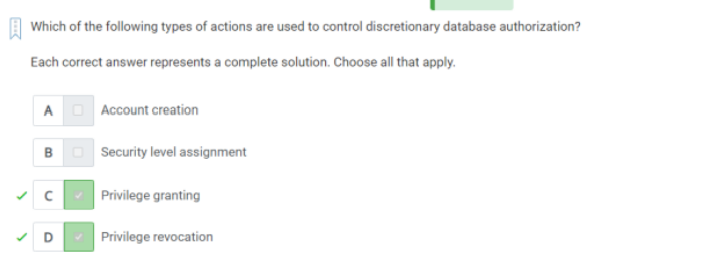
Q56) Which of the following types of actions are used to control discretionary database authorization?
A)
1. Privilege granting
2. Privilege revocation
Q57) in which of the following categories do the physical design decision for indexing fall?
A)
1. Wheather to set up a clustered index
2. What attribute or attributes to index on
3. Whethere to index an attribute
4. Whethere to use a hash index over a tree index
Q58) Which of the following operations takes the results of two queries and returns only those rows that appear in both results sets without eliminations duplicates?
A) INTERSECT ALL
Q59) Which of the following multiset operation do not eliminates duplicates?
A)
1. UNION ALL
2. EXCEPT ALL
3. INTERSECT ALL
Q60) Which of the following rules states that a set of attributes always determines itself or any of its subset?
A) Reflexive



















































Comments
Post a Comment