LAB
Q1) which of the following conditions must be satisfied for a database to be called distributed?
A)
1. Connection of database nodes over a computers network
2. Logical interrelation of the connected databases
Q2) .consider the following figure
Q3) which of the following schemas is the global schema or view, which is the result of integrating all the shareable export schemas?
A) Federated
Q4) which of the following symbols before a tag specifies that the tag can appear as a descendant of the previous tag at any level?
A) //
Q5) which of the following statements are true of the Hbase data model?
A)
1. Only provides low-level CRUD operations
2. Uses the Apache Zookeeper open source system for services
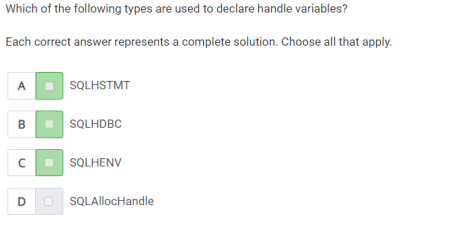
Q6) which of the following types are used to declare handle variables?
A)
1. SQLHSTMT
2. SQLHDBC
3. SQLHENV
Q7) which of the following is an approach that eliminates the generation of a large number of candidate of itemsets?
A) Frequent-pattern-growth algorithm
Q8) which of the following specifies referential grity?
A) FOREIGN KEY clause
Q9) which of the following is the abstraction process whereby classes and objects are uniquely recognizable by means of some identifier?
A) Identification
Q10) which of the following components is a sequence of SQL statements, but it could also be a database transaction or an external program that will be automatically executed?
A) Action
Q12) if a transaction does not overwrite the dirty reads of higher-level transactions, the this transaction has level_____isolation?
Q13) consider the following property;
The changes applied to a database by a committed transaction must persist in the database. These changes must not be lost because of any failure.
Which of the following of transaction possesses the give property?
A) Durability
Q14) which of the following languages is a platform-independent and programming language-independent protocol for massaging and remote procedure calls?
Q15) consider the following statement;
"The cost of transferring reading and writing data blocks between secondary disk storage and main memory buffers."
To which of the following cost components for query execution does the give statement refer to?
A) Access cost to secondary storage
Q16) what are the reasons that Yahoo abandoned Hadoop on Demand?
A)
1. The allocation of a cluster was static.
2. The latency involved in acquiring a cluster was high-a cluster would be granted only when enough nodes were available.
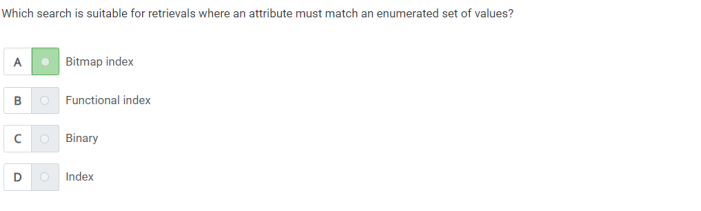
Q17) which search is suitable for retrievals where an attribute must match an enumerated set of valuses?
A) Bitmap index
Q18) which aspect of object specifies how the object is constructed by using the type constructors?
A) Structure
Q19) which of the following statements are true of the Neo4j data model?
A)
1. It has the high-level query language called cypher.
2. It has a graph visualization interface.
3. It can be configured on a cluster of distributed system nodes.
Q20) which of the following are models of spatial information?
A)
1. Field
2. Object
Q21) consider the following rule and then identity its name:
{X-Y,WY-Z}=WX-Z.
A) Pseudotransitive
Q22) which model represents data as record types and also represents a limited type of 1;N relationship called a set type?
A) Network model
Q23) which step of the ER-to-relational mapping algorithm has the foreign key approach and the cross-reference or tionship relation approach?
A) Mapping of binary 1:N relationship types
Q24) which high level or low level DML commands are embedded in a general-purpose programming language, this language is called:
A) host language
Q25) which of the following built-in functions updates attribute sets, the value of the attribute to a new value?
A) Mutator
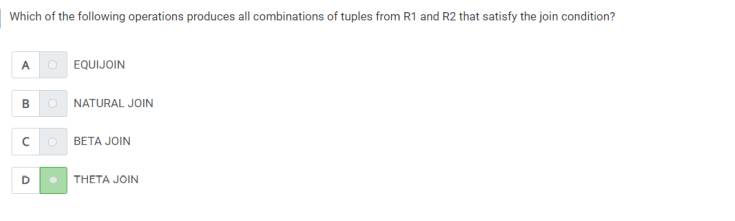
Q26) .which of the following operations produces all combinations of tuples from R1 and R2 that satisfy the join condition?
A) THETA JOIN
Q27) which the following statements are true of functional dependencies?
A)
1. It is a constraint between two sets of attributes from the database.
2. it is a property of the semantics or meaning of the attributes.
3. Each functional dependency is displayed as a horizontal line.
Q28) which provisions are used by the Capacity Scheduler to give each tenant guarantees about cluster capacity?
A)
1.Access control lists that determine who can submit, view, and modify the jobs in a queue.
2. Excess capacity is evenly distributed among active Queues.
Q29) which of the following queries supports regular expressions and pattern matching-based searching in text?
A) Wildcard
Q30) which intention lock indicates the one of more exclusive locks will be requested on some descendant nodes?
A) IX
Q31) Due to which of the following can an attacker attacker impersonate the identity of a legitimate user by obtaining his login credentials?
A) Weak authentication
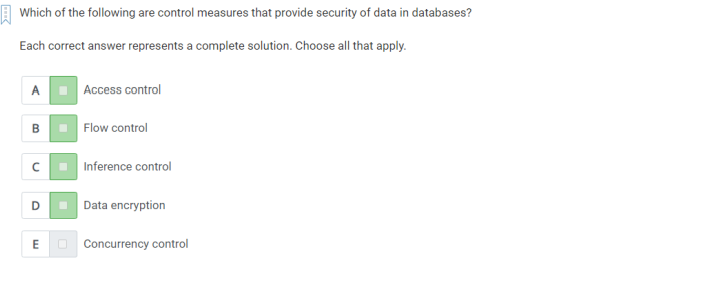
Q32) which of the following are control measures that provide security of data in databases?
A)
1. Access control
2. Flow control
3. Inference control
4. Data encryption
Q33) which of the following symbols represents the PROJECT operation?
A) pi
Q34) .if a file has just been opened or reset, which of the following file operations returns the first record if a condition is specified with the operation; otherwise it returns the next record that satisfies the condition?
A) Scan
Q35) which of the following rules must be enforced when the shared/exclusive locking scheme is used?
A)
1.A transaction must issue the operation read_lock(X) or write_lock(X) before any read _item(X) operation is performance in the transaction.
2. A transaction must issue the operation write_lock(X) before any write_item(X) operation is performed in the transaction.
Q36) which of the following constraints specifies that every entity in a superclass must be a member of a subclass in the specallzation?
A) Total specialization
Q37) which of the following statements are true of DKNF (domain-key normal form)?
A)
1. It takes into account all possible types of dependencies and constraints.
2. Its practical utility is limited.
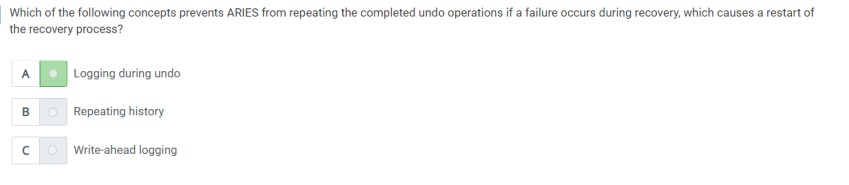
Q38) which of the following concepts prevents ARIES from repeating the completed undo operations if a failure occurs during recovery, causes a restart of the recovery process?
A) Logging during undo
Q39) which RAID level is used for storing logs of transactions?
A) 1
Q40) which of the following constraints is specified between two relations and is used to maintain the consistency among tuples in the two relations?
A) Referential integrity
Q41) mark works as a database administrator in ABC inc. he wants to add a new record in the employees table with the following data:
Employee id as 101.
Employee name as Richard.
Designation as database developer.
Which of the following queries will help him to accomplish the task?
A)
1. Insert into employee value ( 101, 'Richard', 'database developer');
2. Insert into employee ( Employee_id, Name, Designation ) value ( 101, 'Richard', 'Database developer');
Q42) which of the following operations is used to build three-dimensional models, where the topography of a geographical location can be represented with an x,y,z data model?
A) Digital terrain analysis
Q43) which database state satisfies the structure and constraints specified in a schema?
A) Valid state
Q44) which of the following records keeps track of the information about tuples or parameters?
A) Description
Q45) which of the following insertion and deletion rules apply to specialization as a consequence of constraints?
A)
1.Deleting an entity from a superclass implies that it is automatically deleted from all the subclasses to which belongs.
2. Inserting an entity in a superclass implies that the entity is mandatorily inserted in all predicate-defined subclasses for which the entity satisfies the defining predicate.
3. Inserting an entity in a superclass of a total specialization implies that the entity is mandatorily inserted in at lest one of the subclasses of the specialization.
Q46) which of the following applications of data mining includes analysis of creditworthiness of clients and evaluation of fraud detection?
A) Finance
Q47) which of the following information are required for query that retrieval?
A)
1. Files that will be accessed by a query
2. Attributes whose values will be retrieved by a query
3. Attributes on which any selection conditions are specified
Q48) which partitioning corresponds to distributing the tuples across disks based on some partitioning method?
A) Horizontal
Q49) which of the following attributes is considered as a derived attribute?
Name
Age
Birt_date
Phone_no
Address
Which of the following attribution is considered as a derived attribute?
A) Age













































Comments
Post a Comment