FINAL EXAM
1. Who is responsible for identifying data to be stored in the database and for choosing appropriate structures to represent and store
A. Data base designer
3. which of the following DBMS processes stores data on some storage medium that is controlled by the DBMS
A. Constructing
4. which of the following applications analyzes large amount of data to search for the occurrences of specific patterns or relationships ?
A.Data mining
5. during which of the following stages for ereating a database are further specifications provided for storing accessing the database ?
A.Physical Design
6. which model is also known as the CODASYL DBTG model?
A.Network Model
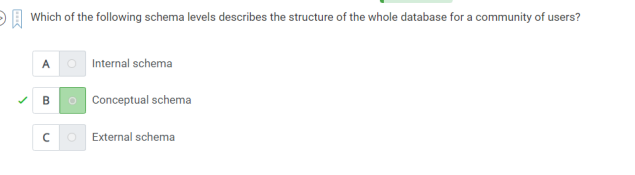
7.which of the following schema levels describes the structure of the whole database for a community of users ?
A. Conceptual Schema
8. in most relational DBMSs there is no specific language that performs the role of
8. in most relational DBMSs there is no specific language that performs the role of
A.SDL
9. which of the following languages specifies the internal schema?
A.SDL
A. Physical
11. Which constraint specifies whether the existence of an entity depends on it being related to another entity via the relationship type?
A.Participation
12. In UML terminology, relationship types are called as _______.
A.associations
13. What attribute can be divided into smaller subparts, which represent more basic attributes with independent meanings?
A.Composite
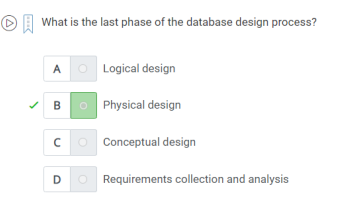
14. What is the last phase of the database design process?
A.Physical Design
15. which of the following notations indicates a specialisation generalization with the disjoint constraint.
A.Blank Triangle
16. Which of the following classes define attribute and operations but does not have object corresponding to those classes
A.Abstract
A.Specialization
18. Which of the following is an Abstraction concept for building composite objects from their component objects.
A.Aggregation
A.Explict
A.Entity integrity
21. which of the following constraints is violated by delete operation.
A.Referential integrity
22. which of the following clauses identify the condition for selecting the tuples from the relations.
A.WHERE
23. Which of the following commands specifies a new relation by giving it a name and specifying its attributes and initial constraints.
A.Create table
A.Select
25. Which of the following joins is the default type of join in a joined table tuple exists in the other relation?
A.Inner
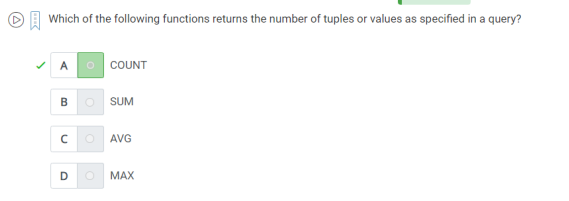
26. which of the following functions returns the number of tuples or values as specified in a query.
A.Count
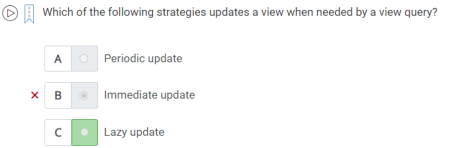
A.Lazy update
A.Sigma
29. which of the following operations comblines the results of two or more SELECT statements without including duplicates.
A.Union
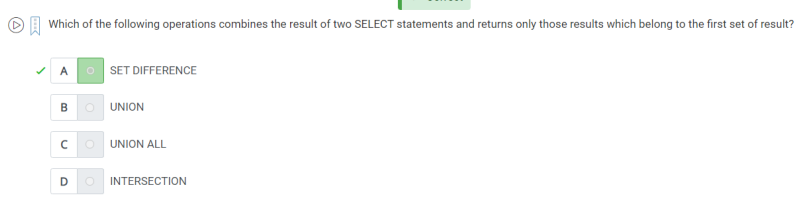
30. which of the following operations combines thee result of two SEELECT statements and returns only those results which belong to the first of result ?
A.Set difference
A.Foreign key
A.Mapping of regular entity types
34. which of the following approaches does not suffer from the impedance same as the database data types ?
A.Database programming language
35. which statements in the SQL standard can be used to invoke stored procedure cither from an interactive interface or from embedded SQL or SQLJ.
A.Call
A.Java servlets
A.DB.php
38. PHP variable starts with a ___ sing.
A.$
A.Life time
40. Which type of literal corresponds to the values of basic data types and is predefined.A.Atomic
41. Which type of constructor creates a collection of key-value pairs, where the value of a key can be used to retrieve the corresponding value?.
A.Dictionary
A.4nf
44. the following Normal forms is violated when a relation has undesirable multivalued dependencies and hence can be use to identify and decompose such relation?.
A.4nf
45. Which of the following buffer replacement strategies works best for certain type of database needed util all the remaining blocks in the relation are processed?
A.MRU
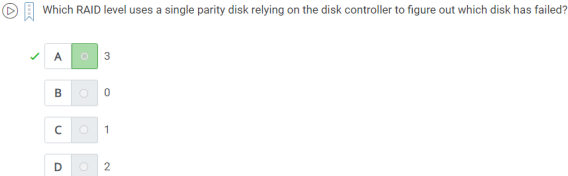
46. which raid level use a single parity disk relying on the disk controller to figure out which disk has failed?
A.3
A.Sorted
A.Contiguous
49. what occurs when the hash field value of Record that is being inserted has to an address that already contains a different record?.
49. what occurs when the hash field value of Record that is being inserted has to an address that already contains a different record?.
A.Collision
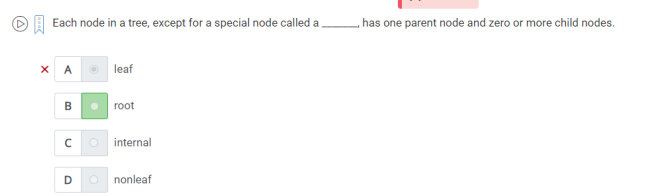
50. each node in a tree expect for a special node called a has one parent node and zero or more child nodes.
A.Root
51. which type of ordered single level index is specified on non ordering fields as additional access structures to improve performance of queries and transactions ?.
A.Secondary
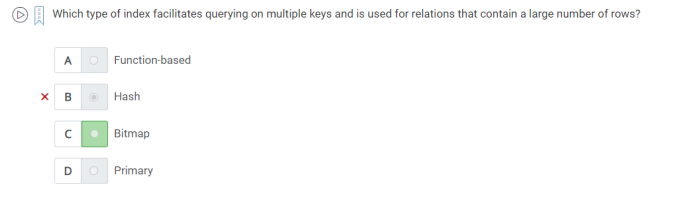
52. which type of index facilitates querying on multiple keys and used for relations that contain a large number of rows.
A.Bitmap
53. which of the following methods ends the iteration after all tuples that can be generated have been generated ?
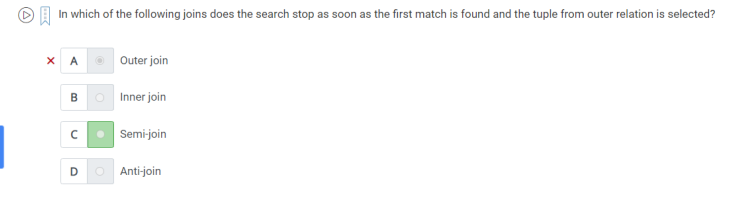
54. In which of the following joins does the search stop as soon as the first match is found and the tuple form outer relation in selected?.
A.Semi join
55. Which search applies to any file but all the methods depend on having appropriate access path selection condition.
A.Linear
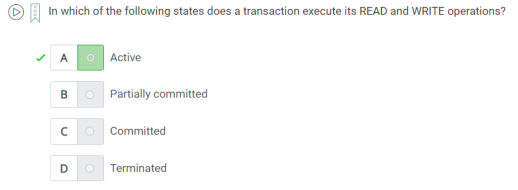
56. what will a transaction be called If database operation a transaction not update the data with but only retrieve data.
A.Read only
A.Active
58. which two phase locking protocol is a deadlock free protocol.
A.Conservative
59. which phase of concurrency control checks whether any of the translation of dates valid serializability.
A.validation
A.Binary
A.NO-UNDO/REDO algorithm
62. which of the following is a specific recovery scheme used in many of IBM’s relational database products ?.
A.ARIES algorithm
63. for which of the following checkpoint actions the fuzzy checkpoint technique coming to use overcome into use to overcome from the action.
A.Suspend execution of transactions temporarily
64. what reduces the contention for CPU and IO services and simultaneously reduces access delays involved in area networks?.
A.Data localization
65. which of the following transparencies is also known as the distribution or network transparency?.
A.Data organizaton
66. which autonomy implies that component DBS has ability to decide whether and how much to share its functionality and resources with other component DBS?.
A.Association
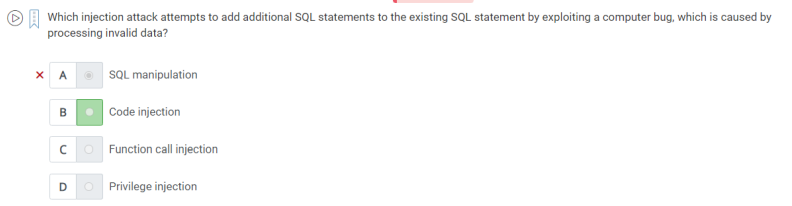
67. when injection attack attempts to add additional SQL statements to the existing SQL statements by exploiting a computer bug which is caused by processing invalid data.
A.Code injection
68.An Administrator who is allowed change student information can update student grades without the instructor s permission.
68.An Administrator who is allowed change student information can update student grades without the instructor s permission.
A.Privilege abuse
69. What type of risk will occur when an attacker floods the server with requests?.
69. What type of risk will occur when an attacker floods the server with requests?.
A.Denial of service
A.a user of prgoram cannot acess data objects who has legitimate right to those objects
71. which of the following control measures is handled by creating user accounts and passwords to control the login process by the DBMS?.
A.Acess control




























































Comments
Post a Comment