You need to design a backup strategy. You need to ensure that all servers are backed up every Friday night and a complete copy of all data is available with a single set of media. However, it should take minimal time to restore data. Which of the following would be the ____
Your source data is of 50 GB. You make a full backup. Next week, once again you perform a full backup, but this time 10 more GB has been added to the source data. Second week, you perform another backup when the source backup has added 30 more GB. What is the total size of backups have you saved till date?
You take a full backup of the source data on Monday. Rest of the week, you take differential backups. What would the differential backup of Friday contain?
When restoring a backup, which of them is likely to be most time consuming to restore?
You are asked to monitor a network which has a network monitoring system. Using the monitoring server, you notice that it is listening on port number 161 for network events. Which network monitoring protocol is in use?
Refer to the following statements. Within the operation of the SNMP protocol, which of the following describes a MIB correctly?
- a database used for managing the entities in a communications network
- it has a hierarchical structure
- provides connectivity via SQL database queries and web interface capabilities
You have added a new device to the network management application. What else should you add to the network management application to be able to control it?
A network administrator is implementing a ping from one end of the network to the other, records the average round-trip time and archives the results. What is most likely being prepared?
What kind of information would you expect to find within a network device’s event log? [Choose all that apply].
Employees are complaining that the network seems to be slow. How could you quantitatively determine if this is the case?
To reduce any kind of network congestion bottleneck, you have configured client-side caching. Which of the following is likely to use this configuration?
You want to monitor the routers for their performance. In case of a performance bottleneck, you need to be alarmed. Which of the following protocol should you use?
Refer to the exhibit. Which of the following configuration is being displayed?
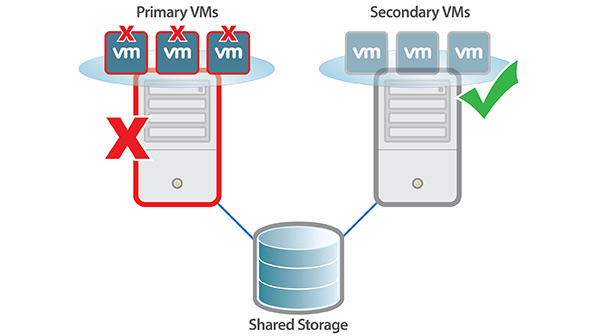
Which of the following is true about Load balancing on a network?
1) Provides redundancy
2) Provides an increase in throughput
3) Increases CPU resources
At what layer of the OSI model do proxy servers operate?
Which of the following criteria can a packet-filtering firewall not use to determine whether to accept or deny traffic?
Who is responsible for the security of hardware on which a public cloud runs?
Which of the following is not one of the AAA services provided by RADIUS and TACACS+?
Which device would allow an attacker to make network clients use an illegitimate default gateway?
Active Directory and 389 Directory Server are both compatible with which directory access protocol?
What information in a transmitted message might an IDS use to identify network threats?
Which policy ensures messages are discarded when they don't match a specific firewall rule?
Which of the following ACL commands would permit web-browsing traffic from any IP address to any IP address?
Which principle ensures auditing processes are managed by someone other than the employees whose activities are being audited?
You have configured a new DHCP server and connected it to the network. There is connectivity to the server, but the clients in the network are unable to obtain IP addresses from the server. Which of the following enabled feature on the switch can cause this issue?
You work in an organization as a network administrator. One of your new clients owns a hotel and has asked you to provide a single Internet connection for every room, but also ensure that the users are not visible to each other. Which technology on the switch will you use to meet the requirements stated in the scenario?
You have empty ports on your switches, that is, no connected hosts. Which of the following are best practices to ensure that the empty ports are secure?
Which of the following versions of SNMP are considered unsecure? [Choose all that apply]
You need to create an access list on your router to filter specific IP addresses and ports. You created entries with permit statements and deny statements. But you forget to add one specific deny statement to filter traffic from host A. How will this traffic be treated?
You work as a network administrator in an organization. The company has three locations. A user is unable to access a shared folder located on a desktop in another location. You try to ping the IP address of the desktop, but it fails. You are unable to ping any IP address from that subnet. What is the next step you should perform on your router?
You have two users who work on the same floor and belong to the same department. The organization has strict rules implemented for printer access. One of the users is unable to access the printer but has access to the Internet. What should you check on your switch?
You have implemented your network with new managed switches. A user is experiencing periodical interruptions on the network. While pinging the main server, you notice that there is periodical packet loss. What could cause this problem?
You have configured a new web server in your network, which will be used only from the local network. You published the website on TCP port 8443 but are unable to access the website on that port from a client device. You are able to ping the server IP address and also have access to the server using a Remote Desktop Connection. What could be the cause of this issue?
You have a complex network environment and have issues related to the routing of network traffic between hosts. Which of the following command will you use to troubleshoot this issue and verify how the packets are routed?


Comments
Post a Comment