Unit 9 Quiz
Unit 10 Quiz
| [Deauth Attack is correct answer ] |
You have been using a wireless router at home. You get an E-mail from the manufacturer that the same router now has been provided with new functionality in its admin interface. You want to get this functionality on the same router without losing existing configuration. What should you do with minimum administrative effort?
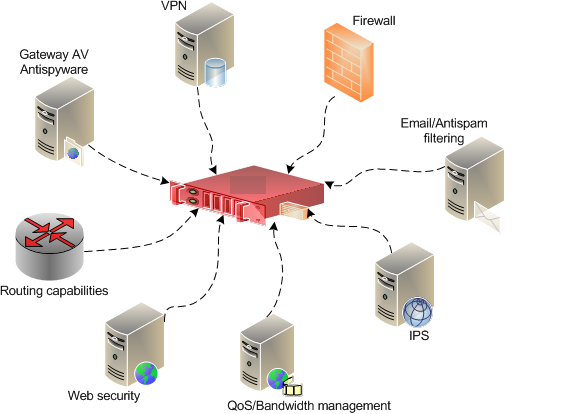
Your organization’s network has multiple layers of security devices. When you attempt to connect to a service on the Internet. However, you receive a security message from the operating system stating that this service is blocked on your workstation. What could be the probable cause?
Your network comprises of multiple switches and a single router. Currently, all users of finance and marketing on the third floor are connected to a flat switch. You must segregate traffic between your finance and marketing groups. You need to ensure that critical finance information can flow without delay to the finance users and ensure additional level of security. What should you do?

Comments
Post a Comment